INTRODUCTION
Every day, private communications, business transactions, and sensitive medical and financial information traverse global information networks -flowing freely through computer databases, across the Internet and telephone lines, and between cellular phones, fax machines, and pagers. Even if you do not use a computer or the Internet every day, information about you is moving through the global Net: your bank records, insurance and medical information, your credit card transactions, and much much more.
While the ability to move information quickly and easily around the world is critical to the future of our economy, it also raises important privacy and security concerns.
These sensitive personal and business communications are vulnerable to the prying eyes of terrorists, hackers, despotic governments, and industrial spies. Without adequate privacy and security protections, the global information infrastructure will never achieve its full potential.
BUT THERE IS A SOLUTION
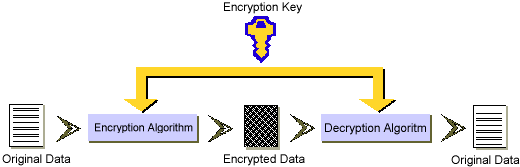
Powerful ENCRYPTION technologies - the locks and keys of the information age - are special programs designed to protect sensitive information on digital communications networks.These techniques are used to safeguard information while it is stored within a network node or while it is in transit across communications media between nodes. So in brief we can say that we need encryption for Privacy and Security.
Definitions:
The concept behind encryption is not that difficult to understand but there are some terms which have to be introduced first so that we can even understand the technical definitions. Following are the definitions of the technical terms associated with encryption:
| Plaintext | An unencrypted message, readable to everyone. |
| Ciphertext | A message that has been encoded by some rule. Only someone who knows what the rule is to decipher the message can read it. |
| Encryption | The procedure of converting plaintext to ciphertext. |
| Cryptosystem | A particular method of converting plaintext to ciphertext. |
| Cryptography | The art of creating and using cryptosystems. |
| Cryptanalysis | The art of breaking cryptosystems, deciphering encrypted messages. |
| Cryptology | The study of both cryptography and cryptanalysis. |
| Key | Some (usually secret) value which, when applied to a particular cryptosystem, deciphers ciphertext and visa versa. |
The term ENCRYPTION has been defined in a thousands of different ways, here are some of the definitions which clearly put forth the concept:
- Encryption is defined as a method in which data or text is encoded so that unauthorized individuals are prevented from accessing it.
- Data Encryption is the coding of data or messages to prevent them from being understood by unauthorized persons.
- Encryption is a fundamental security mechanism in which ordinary data, or plain text, are transformed by the encryption process into cipher text.
A simple example of a cryptosystem is to shift the letters of the alphabet by a number, say 2. Using this rule the message:
attack at dawn
would become:
cvvcem cv fcyp
Here n is the key, which is 2 in this case. Here we have, we can say in layman's language, locked our information by a key which is equal to 2. This lock can only be opened by the person who has that key. This is fundamentally how encryption really works.
ALL ABOUT ENCRYPTION
Traditionally, several methods can be used to encrypt data streams, all of which can easily be implemented through software, but not so easily decrypted when either the original or its encrypted data streams are unavailable.
The simplest of all the methods is the Translation Table. In a translation table, each 'chunk' of data (usually 1 byte) is used as an offset within the table, and the resulting 'translated' value from within the table is then written into the output stream. The encryption and decryption programs would each use a table that translates to and from the encrypted data. While this method is very simple and fast, the down side is that once the translation table is known, the code is broken. But there are mainly two types of encryptions: symmetric encryption, and public key encryption. Symmetric encryption uses a symmetric key. Public key encryption uses a pair of keys, called public/private keys.
Symmetric Encryption

Symmetric keys are generated quite often. For example, browsers generate new symmetric keys each time they open a secure transaction. Symmetric encryption is relatively fast and small. However, if you need to transmit the data to someone else, they must have the exact same key that you used to encrypt the data.
Public Key Encryption
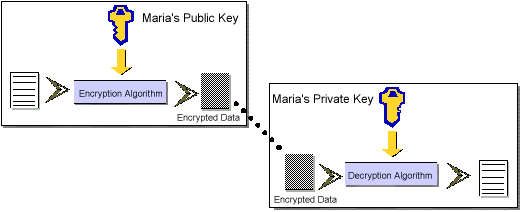
The user gives his or her public key to others, and keeps the private key. It is okay for you to give your public key to others without compromising your security; it is very difficult to figure out a private key from a public key.
Problem: Public/private encryption is bulky and slow.
Symmetric and Public/Private Encryption both together
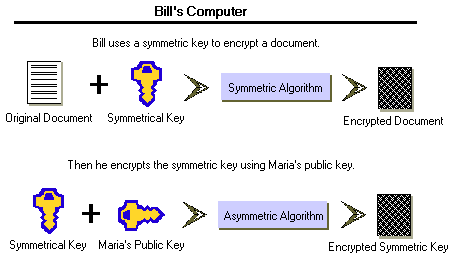
Public/private key pairs are very long. They are time consuming and can make files much larger than their normal size. To make the process fast and secure, public key encryption is used in conjunction with symmetric key encryption.
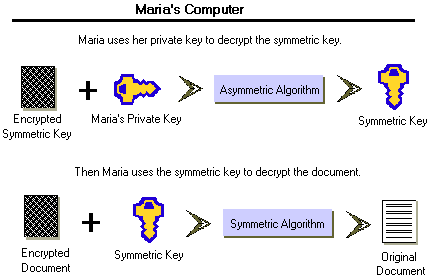
When you have a message to encrypt, use a symmetrical key to encrypt it. Then encrypt the symmetrical key with the receiver's public key. When the receiver gets the encrypted message and key, she uses her private key to decrypt the symmetrical key. Then she uses the symmetrical key on the message.
The strength of the encryption depends on the length of the key used. The length of the key is measured in "bits". Each bit can be turned on or off. In symmetric key encryption, each extra bit doubles the strength of the key. Asymmetric encryption is more complicated, but longer keys are generally stronger than shorter keys.
PGP
The popular PGP (Pretty Good Privacy) public key encryption, uses an asymmetrical key or rather public/private keys. PGP, created by Philip Zimmermann, is the de facto standard program for secure e-mail and file encryption on the Internet. Its public-key cryptography system enables people who have never met to secure transmitted messages against unauthorized reading and to add digital signatures to messages to guarantee their authenticity.
Why do we need PGP? E-mail sent over the Internet is more like paper mail on a postcard than mail in a sealed envelope. It can easily be read, or even altered, by anyone with privileged access to any of the computers along the route followed by the mail. Hackers can read and/or forge e-mail. Government agencies eavesdrop on private communications.
The most common method of breaking ciphers is by a brute-force attack. This sort of attack involves running through possible combinations of keys and applying them to the cryptosystem until the message is decrypted. It is the same as trying to guess a PIN for someone's keycard by going through all the possible combinations of numbers. It is said that any University computer science major would have enough computer power available to be able to break most 56-bit key cryptosystems in less than one week.
DES
The private sector began to feel the need for cryptographic methods to protect their data. DES (Data Encryption Standard) was thus developed in the 1970s resulting from the pressure put by the private sector on the US government. DES is an algorithm developed by the National Institute of Standards and Technology for encrypting and decrypting data.
IBM developed the original ideas behind the Data Encryption Algorithm (DEA) in the 1960s.
The DEA performs a transformation on a block of 64 bits using a 56 bit key, that is it takes 64 bits of the plain text (data to be encrypted) and changes it into a different 64 bits (the cipher text), using a key (known only by the person 'sending' the 'message' and the person 'receiving' it). It does this in several steps, using several kinds of transformations.
When originally proposed, the length of the key in DES was 64 bits. Before it was made the standard, this was again revised to be only 56 bits. Why the change? It is suspected that by decreasing the standard key size, any key can be broken with a little less difficulty by super computers which are affordable only to a country's government. So in a way, the US government is suspected to have intentionally made this change so that they can break any key and derive any secret information which they suspect to be dangerous for National Security purposes.
The other controversial aspect of the release of the DES was that the complete design criteria were never published. Since not all of the steps in the algorithm seem logical, or obvious, this is slightly suspicious. Could the government somehow have encoded a trapdoor into the algorithm?
BIG BROTHER
Right now, the FBI and the Clinton Administration are pushing for sweeping new domestic encryption controls and broad new surveillance powers which would strip American citizens of their right to privacy and security in the information age.
The FBI and its supporters in Congress are demanding legislation to ban any encryption program that does not contain government approved back doors or other features that give an extra copy of your encryption keys to a government-approved third party.
Also a requirement that all new homes built in the United States contain surveillance cameras that could be activated remotely by the government if you were ever suspected of committing a crime.
Sounds like fiction? It's not.
CONCLUSION
Encryption, or rather Cryptography, is a part of our day-to-day life operations. Making encryption techniques as hard as possible to break is the job of a good cipher designer and it is extremely necessary for a safer society. But is a BIG BROTHER really needed?